Technical User
Using the Developer Portal API with a Technical User
The distinction between the frontend and the console API lies in the way users can interact with the developer portal.
The frontend provides a graphical user interface (GUI) that allows users to interact with the portal using a web browser. This is the main way that users will interact with the portal and perform tasks such as creating Apps, adding products and submitting activation request.
On the other hand, the console API allows users to interact with the portal programmatically, using command line tools or scripts. This is an alternative method to interact with the portal, and is primarily intended for power users or automated workflows. Using the console API, users can perform tasks such as creating Apps, adding products and managing activation request through code rather than through the GUI.
- A technical user is associated with an organization and is not directly connected to a real user.
- A user of an organization with administrative privileges can create a technical user and access the portal via an access token to connect to the portal's API.
- A user of an organization can view all technical users associated with their organization.
Access Workflow
How to Create the Technical User
To use the technical user, you must first generate a technical user in the "Settings" menu.
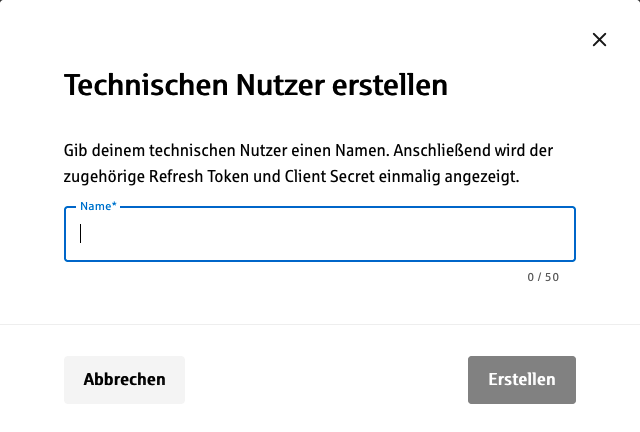
Create a Technical User
- Give a name to the technical user and
- create a new one using the "Create" button.
Example:
 |
|---|
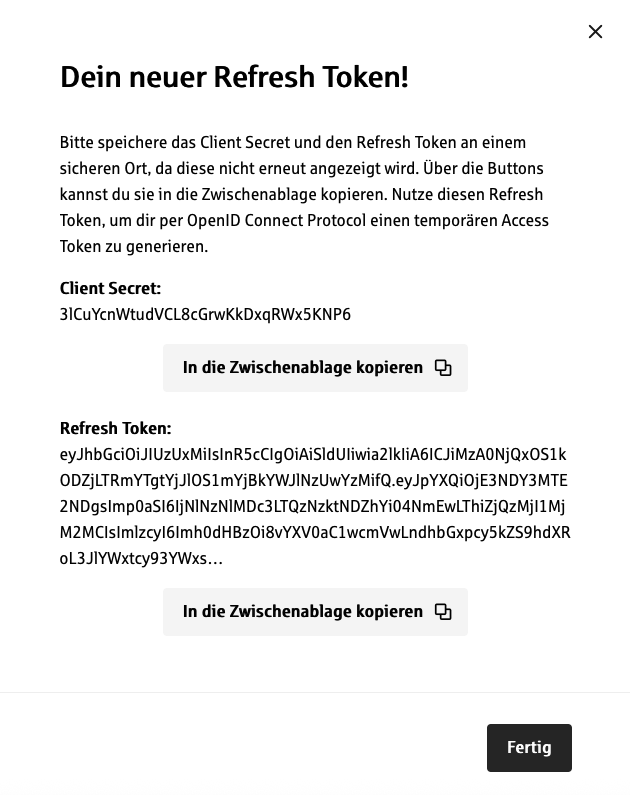
- A modal will open displaying the client secret and refresh token.
Example:
 |
|---|
- Save the client secret and the refresh token securely, e.g. in a password manager. This will only be displayed here. You need the client secret and the refresh token to get an access token at the Identity Access Management server (IAM server) to access the Developer Portal API.
The client secret and refresh token will be displayed to you once, so please make sure to save it carefully!
Getting Access Tokens from the Identity Access Management Server
To access the Developer Portal API, you need an access token, which you can get from the IAM server (Keycloak). The access token has a duration of 2 hours and must be renewed after expiration at the IAM server.
Information required to access the IAM server
- Client-Id (can be found in the settings of your technical user)
- Client-Secret (was shown to you when generating the technical user, and you saved it safely)
- Refresh-Token (was also displayed when generating the technical user, and you have stored it safely with you)
- Token-Endpoint/URL (can be found in the settings of your technical user under interface)
- Grant-Type (is always "refresh_token")
Accessing the IAM Server
The IAM server is connected via API (Application Programming Interface). See also the current Keycloak (IAM server) documentation.
| Eingabe | Parameter | Wert |
|---|---|---|
| Token-Endpoint/URL | POST | <server>/auth/realms/<realm>/protocol/openid-connect/token |
| Header | Content-Type | application/x-www-form-urlencoded |
| Header | Accept | application/json |
| Body | client_id | <client_id> |
| Body | client_secret | <client_secret> |
| Body | refresh_token | <refresh_token> |
| Body | grant_type | refresh_token |
Example:
Access Data:
Client-Id: 2ce233b7-9349-44d9-8e38-0a88090115d5
Client-Secret: asQx6IsK7hGGaUQIpE7bWEEjr72CGML9
Refresh-Token: eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICI2NmI5NzBkZC01ZDQyLTQ1ZGYtYjFkMi03Mjc1YzU5ZDI4YmMifQ.eyJpYXQiOjE2OTM5OTcyNDgsImp0aSI6ImM0MWE3ODk5LWI1NDAtNDcyOC05NDBhLWNkZmE2MmNjMGUzZCIsImlzcyI6Imh0dHA6Ly9sb2NhbGhvc3Q6OTA4MC9hdXRoL3JlYWxtcy93YWxsaXMiLCJhdWQiOiJodHRwOi8vbG9jYWxob3N0OjkwODAvYXV0aC9yZWFsbXMvd2FsbGlzIiwic3ViIjoiMzc3OWVlYjctZjllMi00ZTZkLTg4ZTQtZTBlZjFlZTg3NGEwIiwidHlwIjoiT2ZmbGluZSIsImF6cCI6IjJjZTIzM2I3LTkzNDktNDRkOS04ZTM4LTBhODgwOTAxMTVkNSIsInNlc3Npb25fc3RhdGUiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUiLCJzY29wZSI6InByb2ZpbGUgZW1haWwgb2ZmbGluZV9hY2Nlc3MiLCJzaWQiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUifQ.JitaPbbqb9wVwXzooofxPILL_JCuIkr5KzfVWTV_mL8
Token-Endpunkt/URL: http://localhost:9080/auth/realms/wallis/protocol/openid-connect/token
Request (cURL):
curl --location 'http://localhost:9080/auth/realms/wallis/protocol/openid-connect/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Accept: application/json' \
--data-urlencode 'client_id=2ce233b7-9349-44d9-8e38-0a88090115d5' \
--data-urlencode 'client_secret=asQx6IsK7hGGaUQIpE7bWEEjr72CGML9' \
--data-urlencode 'refresh_token=eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICI2NmI5NzBkZC01ZDQyLTQ1ZGYtYjFkMi03Mjc1YzU5ZDI4YmMifQ.eyJpYXQiOjE2OTM5OTcyNDgsImp0aSI6ImM0MWE3ODk5LWI1NDAtNDcyOC05NDBhLWNkZmE2MmNjMGUzZCIsImlzcyI6Imh0dHA6Ly9sb2NhbGhvc3Q6OTA4MC9hdXRoL3JlYWxtcy93YWxsaXMiLCJhdWQiOiJodHRwOi8vbG9jYWxob3N0OjkwODAvYXV0aC9yZWFsbXMvd2FsbGlzIiwic3ViIjoiMzc3OWVlYjctZjllMi00ZTZkLTg4ZTQtZTBlZjFlZTg3NGEwIiwidHlwIjoiT2ZmbGluZSIsImF6cCI6IjJjZTIzM2I3LTkzNDktNDRkOS04ZTM4LTBhODgwOTAxMTVkNSIsInNlc3Npb25fc3RhdGUiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUiLCJzY29wZSI6InByb2ZpbGUgZW1haWwgb2ZmbGluZV9hY2Nlc3MiLCJzaWQiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUifQ.JitaPbbqb9wVwXzooofxPILL_JCuIkr5KzfVWTV_mL8' \
--data-urlencode 'grant_type=refresh_token'
Response (json):
{
"access_token": "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJ3ZW1CbzNZdGZTdXdhbWFkbEdXRXEwaVV2b25seVdwMGZ6X2dIaHJpenVVIn0.eyJleHAiOjE2OTQwMDQ3MTksImlhdCI6MTY5Mzk5NzUxOSwianRpIjoiNWFkOTM1MjUtMGQ4Ni00MWZlLWI0NjUtZGJmYTRiNTJlMjFjIiwiaXNzIjoiaHR0cDovL2xvY2FsaG9zdDo5MDgwL2F1dGgvcmVhbG1zL3dhbGxpcyIsInN1YiI6IjM3NzllZWI3LWY5ZTItNGU2ZC04OGU0LWUwZWYxZWU4NzRhMCIsInR5cCI6IkJlYXJlciIsImF6cCI6IjJjZTIzM2I3LTkzNDktNDRkOS04ZTM4LTBhODgwOTAxMTVkNSIsInNlc3Npb25fc3RhdGUiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUiLCJhY3IiOiIxIiwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbIm9mZmxpbmVfYWNjZXNzIiwiZGVmYXVsdC1yb2xlcy13YWxsaXMiLCJ1bWFfYXV0aG9yaXphdGlvbiJdfSwic2NvcGUiOiJwcm9maWxlIGVtYWlsIG9mZmxpbmVfYWNjZXNzIiwic2lkIjoiN2IyMmQzMDQtNDYwNC00NjU5LTgzMWItZGQ3NjIzMmQ0Y2Q1IiwiZW1haWxfdmVyaWZpZWQiOnRydWUsIm5hbWUiOiJCZWlzcGllbC1OdXR6ZXIiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiIwMTg3YmVmNS05Mjg2LTRhZGYtYTkzNy0zNjhlODlhNGFkZjEiLCJmYW1pbHlfbmFtZSI6IkJlaXNwaWVsLU51dHplciJ9.lAZwuSDc8yxm_jKSWxm6mxdTeFVmH5wGclsCE-TlIsoSdfIhOhfMSKd5Dwep4CQ6vpGLsX8tVjTEvkVyAzZMXeB3sHq8tCUsc0kMpINBxYeWanCSh6iVXM30ybyiYR8AkVxykcvcquzYkxPHT2nuMTMoMVPCRNg1SzjSyjQ3pa9J81yc7G5ksajH_4wIXYeX0TX-ZzT5U4d3GTfl3iIVU4B-TwqETTYETIz_3pAIHvLCtxwamI1ETenNG9y0k0hPuS0Wq9d0R8BVEnp1cbKNGxVx5dYDSoPFHPtNj_cGnQPZF_q9y4z9UCebkHBmKMA5bP2YA-Hl5edotgamHKCt0g",
"expires_in": 7200,
"refresh_expires_in": 0,
"refresh_token": "eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICI2NmI5NzBkZC01ZDQyLTQ1ZGYtYjFkMi03Mjc1YzU5ZDI4YmMifQ.eyJpYXQiOjE2OTM5OTc1MTksImp0aSI6IjZhMjliZmViLTM2NmQtNDIzOC1hZmExLWEyZjk1MGNlNGRhMSIsImlzcyI6Imh0dHA6Ly9sb2NhbGhvc3Q6OTA4MC9hdXRoL3JlYWxtcy93YWxsaXMiLCJhdWQiOiJodHRwOi8vbG9jYWxob3N0OjkwODAvYXV0aC9yZWFsbXMvd2FsbGlzIiwic3ViIjoiMzc3OWVlYjctZjllMi00ZTZkLTg4ZTQtZTBlZjFlZTg3NGEwIiwidHlwIjoiT2ZmbGluZSIsImF6cCI6IjJjZTIzM2I3LTkzNDktNDRkOS04ZTM4LTBhODgwOTAxMTVkNSIsInNlc3Npb25fc3RhdGUiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUiLCJzY29wZSI6InByb2ZpbGUgZW1haWwgb2ZmbGluZV9hY2Nlc3MiLCJzaWQiOiI3YjIyZDMwNC00NjA0LTQ2NTktODMxYi1kZDc2MjMyZDRjZDUifQ.qx9jDQnBIrznqsQulbfQsjpo4DlSCDErZ6vneBEqf0I",
"token_type": "Bearer",
"not-before-policy": 0,
"session_state": "7b22d304-4604-4659-831b-dd76232d4cd5",
"scope": "profile email offline_access"
}
After that, the access token can be used to access the Developer Portal API. After 2 hours have passed a new access token must be requested from the IAM server (see also Access Workflow).